We use media monitoring and risk intelligence platforms to collect, process, analyze, and generate risk intelligence. We issue timely security risk alerts as necessary to employees based at our overseas projects, as well as those on international business trips, and carry out travel risk management. At the same time, such information also provides objective and credible benchmarks for the design of security systems, and viable intelligence for management decisions.
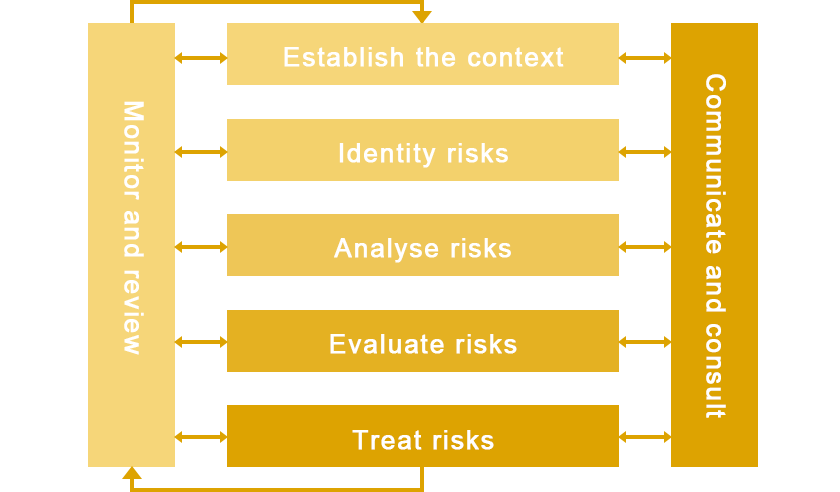
We assess our baseline security risk management and the risk levels of our projects following ISO 31000 standards, as well as security risk assessment models recognized by the international security industry, including elements set by international security experts, and formulated corresponding mitigation measures. Further details on our security risk management are articulated in our Security and Human Rights Policy, Guidelines on the Principles of the Use of Security Force Overseas, Guidelines on Security Facilities and Security Forces for Overseas Projects, and other security management policies, baseline security standards, and crisis management plans.