In terms of data security, we face risks of external attacks or internal misuse, as well as the possibility of data tampering during transmission and processing, which may severely affect data accuracy and reliability. To address this, we employ Continuous Data Protection (CDP) technology to effectively safeguard data security. With increasing reliance on information systems for business operations, availability risks have become more prominent. To control such risks, we have formulated a Business Continuity Plan (BCP), established a "two locations, three centers" disaster recovery system, and provided hot standby support for critical business information systems to ensure business continuity and stability.
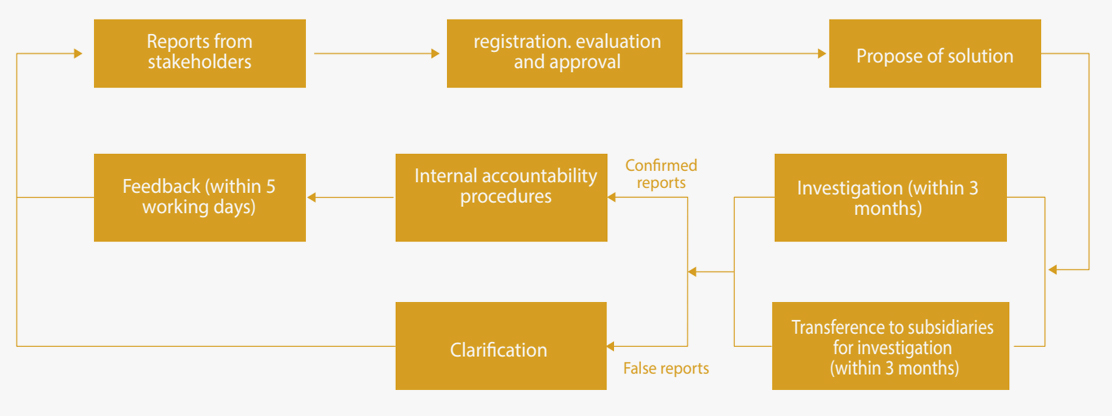
For information security and privacy breach emergencies, we have developed the Incident Response Plan for Information Security Emergencies, which specifies the severity levels of various information security incidents (such as network outages and equipment failures), as well as emergency reporting, disposal, and information disclosure procedures. We organize disaster emergency and backup recovery drills every six months. Meanwhile, we have clarified the reporting procedures and time limits for information security emergencies: on-site personnel shall immediately report to the department head → the department head shall notify relevant personnel for on-site disposal and proceed with the procedures immediately. Reports shall be directly submitted to leadership, and in necessary cases, directly to the enterprise's principal responsible person. Upon receiving reports of information security incidents, the enterprise's principal responsible person or direct management leader shall promptly organize a response and report to the company's emergency duty office, and report to local government/public security authorities when necessary.
We also conduct information security awareness training covering all employees through various means, including annual special events on information security and privacy protection, and irregularly releasing updates on information security and privacy protection on work platforms. For employees who violate information security management regulations or fail to fulfill information security responsibilities, disciplinary measures shall be taken in accordance with the Administrative Disciplinary Measures, depending on the circumstances. Additionally, information security and privacy protection are incorporated into the performance evaluation of subsidiaries, accounting for 10% of the total assessment.